Local, Remote and Web Access to the Program
The program has a client/server architecture. The server works as a Windows service to monitor hosts, send notifications and generate reports. The client is a Windows application with a GUI that allows you to connect to the server and manage the monitored hosts, review statistics, change settings, etc. When installing the program, you can select to install the server, the client, or both. Thus, you can install the client and the server on the same PC or different PCs.
It is recommended to install the Ping Monitor server on a Windows server or another computer that is always on, so monitoring can run in the 24/7 mode. The Ping Monitor GUI client can be installed on the same or a different computer, since the program allows clients to connect to the server remotely over a LAN/WAN/VPN. You can install multiple clients that can connect to the same server and work concurrently. To be able to connect to the server remotely, you need to open ports 48030 and 48031 in the firewall on the computer where the server is installed.
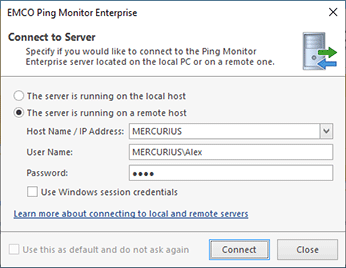
When running the Ping Monitor client, you should specify if you would like to connect to a server installed locally or remotely Pic 1. If you wish to connect to a remote server, you should enter its host name or IP address.
The program supports different numbers of simultaneous client connections depending on the used license. The Free edition of the program supports only one connection, the Professional edition supports two connections, and the Enterprise edition doesn't limit the number of simultaneous connections.
The server requires user authentication, so when using the default settings, you need to specify a Windows account that is a member of the Administrators group on the computer where the server is installed. If your current Windows session satisfies this condition, you can enable the Use Windows session Credentials option and skip entering the username and password.
The program allows you to configure who has access to the server. You can allow access for selected Windows users/groups and can assign different roles in the program to different users. For example, you can provide an administrative access with all permissions to a specific user group and a read-only access to all other users. You can learn more about using roles and permissions in the Access Control chapter.
The program uses secure communication between the client and the server, so all the data traffic is encrypted. By default, the program uses a self-signed SSL certificate, and you get a warning that the used certificate isn't trusted when you connect to the server. If you have a SSL certificate, it's recommended to specify it in the program preferences to validate the identity of the server when connecting to it remotely.
Monitoring Web Interface
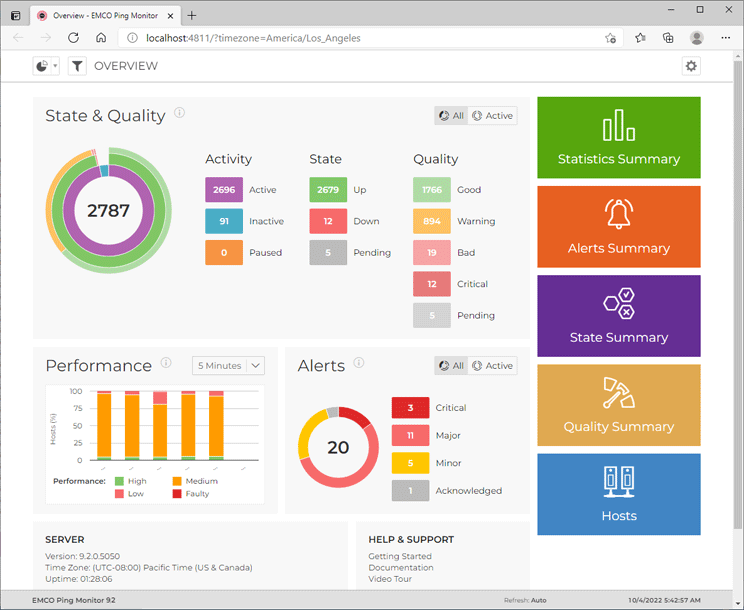
In addition to the GUI client, you can also use the monitoring web interface that offers features similar to those available in the GUI client. The web interface allows you to review the state and quality of the monitored hosts, get detailed host statistics and start/stop monitoring of hosts and groups Pic 2. The current version of the program doesn't allow managing hosts and settings through the web, so you need to use the GUI client to add/delete hosts and to change the program settings.
The program uses Microsoft IIS to deploy the monitoring web interface. During installation of Ping Monitor, the program installer automatically activates Microsoft IIS and deploys the monitoring web interface if you choose to install it. When installed with default parameters, a corresponding shortcut appears in the Windows Start menu, and you can use it to open the monitoring web interface in a browser.